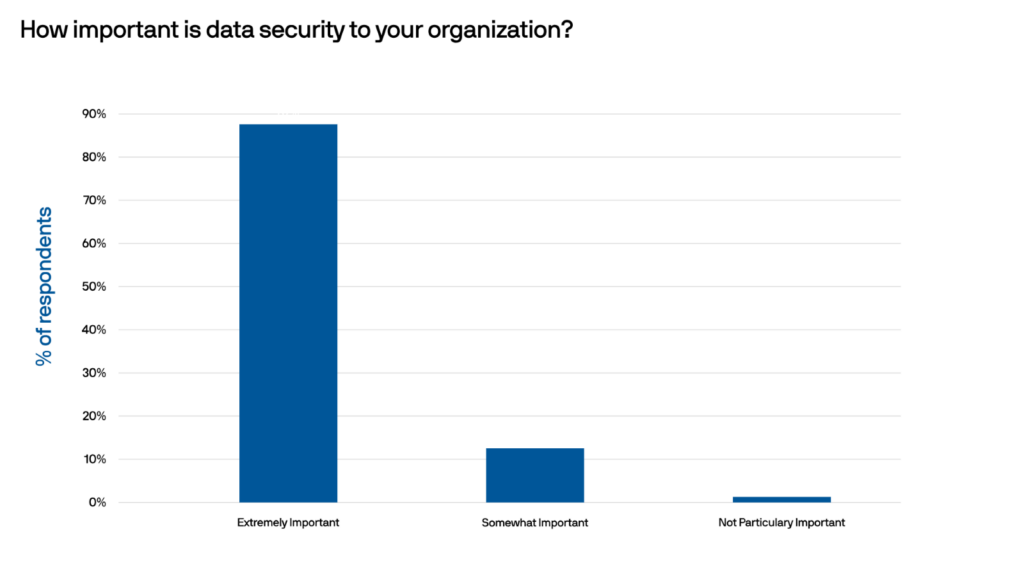
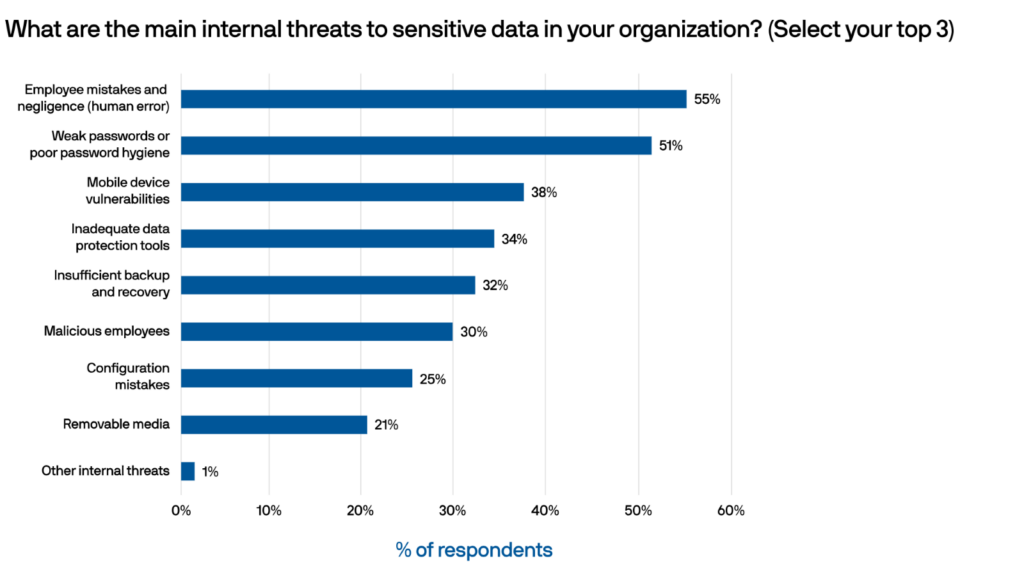
This blog explores multi-factor authentication (MFA), a security method that adds layers of verification to ensure digital accounts are secure. Learn how MFA works and discover real-world examples demonstrating its importance in safeguarding sensitive information!
What is multi-factor authentication (MFA)?
Multi-factor authentication (MFA) is a digital security measure designed to enhance the protection of online accounts and sensitive data by requiring multiple forms of verification from the user before granting access.
Unlike traditional single-factor methods that rely solely on a password, MFA combines two or more of the following:
- Something you know. Includes passwords, PINs, or any other knowledge-based information that only the authorized user should know.
- Something you have. Involves physical devices such as smartphones, security tokens, or smart cards uniquely tied to the user and generates temporary access codes.
- Something you are. Biometric identifiers like fingerprints, facial recognition, or retinal scans provide a highly personal and difficult-to-replicate layer of authentication.
The synergistic use of these factors significantly reduces the risk of unauthorized access. Even if one factor is compromised, the attacker must still breach the remaining layers to gain entry.
This approach fortifies digital security by adding multiple hurdles for potential intruders to overcome. MFA is pivotal in safeguarding sensitive accounts, data, and systems across various online platforms, providing users with greater peace of mind in an increasingly dangerous digital landscape.
How does multi-factor authentication work?
Multi-factor authentication (MFA) is an additional layer of security that goes beyond the traditional username and password approach. It’s a sophisticated digital security technique that requires users to verify their identity through multiple diverse factors, adding layers of protection beyond passwords alone.
MFA is widely used across various online services, from email and social media platforms to banking and corporate systems, to ensure that only legitimate users can access sensitive information.
Here’s how MFA typically functions:
- User initiation. The user initiates the login process by entering their username, email, and initial password.
- First factor verification. The system prompts the user to provide the first factor of authentication, typically something they know, such as a password or PIN.
- Second factor verification. After successfully passing the first factor, the user is prompted to provide a second verification form. This could be something they have, like a temporary code sent to their smartphone via SMS or a mobile app, or something they are, like a fingerprint or facial scan.
- Authentication confirmation. Once both factors are validated, the system confirms the user’s identity and grants access to the requested account or system.
Six common multi-factor authentication methods
Each kind of MFA method enhances security by requiring multiple independent proofs of identity. Choosing the right method depends on factors such as user convenience, the necessary level of security, and potential vulnerabilities associated with specific types of data.
The most common methods of multi-factor authentication include:
1. SMS or email codes
How it works: A one-time code is sent to the user’s registered mobile number or email. The user enters this code along with their password during login.
Benefits: Widely accessible, simple to implement, and provides an extra layer of security beyond passwords. However, it can be susceptible to SIM swapping or email account compromise.
2. Authentication apps (TOTP)
How it works: Time-based one-time password (TOTP) apps like Google Authenticator or Authy generate temporary codes synced with the user’s account. These codes change every 30 seconds and are entered with the password during login.
Benefits: Works offline, immune to most phishing attacks, and reduces reliance on network connectivity. Offers enhanced security compared to SMS codes.
3. Biometric verification
How it works: Utilizes unique biological traits like fingerprints, facial recognition, or iris scans to confirm the user’s identity.
Benefits: Highly secure and user-friendly, as biometric identifiers are challenging to replicate. Enhances convenience while maintaining a strong security layer.
4. Hardware security keys
How it works: Physical devices (USB keys) are plugged into the user’s device and require a physical tap or button press for authentication.
Benefits: Extremely secure due to the offline nature and reliance on cryptographic protocols. Immune to most online attacks and phishing.
5. Push notifications
How it works: A notification is sent to the user’s registered device upon login. The user approves or denies the login attempt from the notification itself.
Benefits: Convenient and user-friendly. Offers real-time interaction for immediate verification decisions.
6. Smart cards
How it works: Users possess a physical card with embedded chips. Inserting the card into a reader or tapping it against a contactless reader validates identity.
Benefits: High level of security, especially for enterprise environments. Cards can hold digital certificates and require physical presence for authentication.
7. Backup codes
How it works: A set of single-use codes is provided to the user during setup. These codes can be used if primary authentication methods are unavailable.
Benefits: Useful when other methods are inaccessible, ensuring continued access. Acts as a contingency plan.
Multi-factor authentication examples
MFA is used in a variety of different industries and scenarios. Here are a few areas where MFA is commonly implemented.
Business network access
Multi-factor authentication is often employed in a corporate setting to secure employees’ access to sensitive business networks and data. When employees log in to their work accounts from remote locations or within the company premises, MFA provides an extra layer of protection.
Typically, authentication methods, such as authentication apps (TOTP), which generate time-based one-time passwords for entry, and biometric verification, like fingerprint scanning, are used. This approach ensures that only authorized personnel can access confidential company information and resources, safeguarding against unauthorized data breaches or cyberattacks.
Healthcare patient portals
Healthcare providers implement MFA on patient portals to ensure the privacy and security of personal medical records and sensitive health information.
Patients accessing their health records, scheduling appointments, or communicating with medical professionals must often undergo a two-factor authentication process. This might involve SMS or email codes sent to the user’s registered mobile number or email address and biometric verification such as facial recognition.
By employing MFA, healthcare institutions can maintain the confidentiality of patient data and comply with regulatory requirements while enabling convenient access for patients.
E-Commerce transactions
MFA plays a pivotal role in safeguarding financial transactions and customer accounts in online shopping. When making purchases or managing accounts on e-commerce platforms, customers may encounter MFA during checkout or account login.
A combination of SMS or email codes and push notifications can be utilized, allowing customers to confirm their identity before completing a transaction. This approach protects against unauthorized credit card use and fraudulent account access, enhancing customer trust and ensuring the security of their financial activities.
Seven benefits of multi-factor authentication
Industries across the spectrum recognize the imperative of fortifying digital security measures. For most companies, implementing multi-factor authentication brings many benefits that safeguard sensitive data and foster trust and resilience in the face of cyber threats.
Below are seven important benefits of MFA:
- Enhanced data security. Protects sensitive client information and proprietary data from unauthorized access or breaches.
- Regulatory compliance. Helps meet industry-specific data security regulations and standards.
- Reduced fraud and hacking. Mitigates the risk of fraudulent transactions and cyberattacks targeting financial and personal information.
- Customer trust. Instills confidence in clients by demonstrating a commitment to robust security practices.
- Secure remote access. Enables secure remote access to company resources, critical for industries with a remote or distributed workforce.
- Preservation of intellectual property. Safeguards valuable intellectual property from unauthorized dissemination or theft.
- Streamlined authentication. Balances security and usability, ensuring efficient access for authorized users while maintaining stringent protection.
Five multi-factor authentication best practices
Multi-factor authentication (MFA) is a cornerstone of a robust data security policy, offering a proactive defense against the risks of unauthorized access and cyber breaches.
Here are five multi-factor authentication best practices to enhance your data security:
- Comprehensive coverage. Apply MFA to all critical access points, including remote logins, sensitive databases, and administrative privileges, to ensure a holistic defense against unauthorized entry.
- Diverse authentication factors. Utilize a mix of authentication factors (knowledge-based, possession-based, biometric) to create a multi-layered defense, reducing the likelihood of compromise through a single point of failure.
- Regular review and updates. Routinely assess MFA methods and their effectiveness and update them as needed to stay aligned with evolving security threats and technological advancements.
- User-friendly experience. Choose MFA methods that balance security with user convenience, promoting user adoption and minimizing the risk of circumvention due to frustration.
- Continuous user education. Educate users about the importance of MFA, potential threats, and proper authentication practices to empower them to be proactive participants in maintaining a secure digital environment.
Interested in hearing more about our report’s findings? Click here for access to the full report!