As we travel deeper into the digital age, businesses and institutions increasingly rely on advanced technologies to drive efficiency and productivity. However, with these advancements come vulnerabilities that unscrupulous individuals may exploit.
Insider threats pose a unique challenge, as they originate from individuals who, at first glance, seem entirely trustworthy and have legitimate access to sensitive information and systems.
According to the U.S. Government, “An insider threat is defined as the threat that an employee or a contractor will use his or her authorized access, wittingly or unwittingly, to do harm to the security of the United States.” While government, military, and defense organizations are often at the forefront of insider threats, in truth, they can occur at any kind of organization.
The WinZip® Enterprise team recently completed a survey that clarified the growing concern of cyber security in business. The study’s conclusive results underscore the paramount importance of organizations taking swift and decisive action to confront insider security risks.
In this blog, we will explore insider threats, delving into various facets and shedding light on potential consequences. From identifying the different types of insider threats to understanding their motivations, we’ll provide you with the knowledge to safeguard your organization.
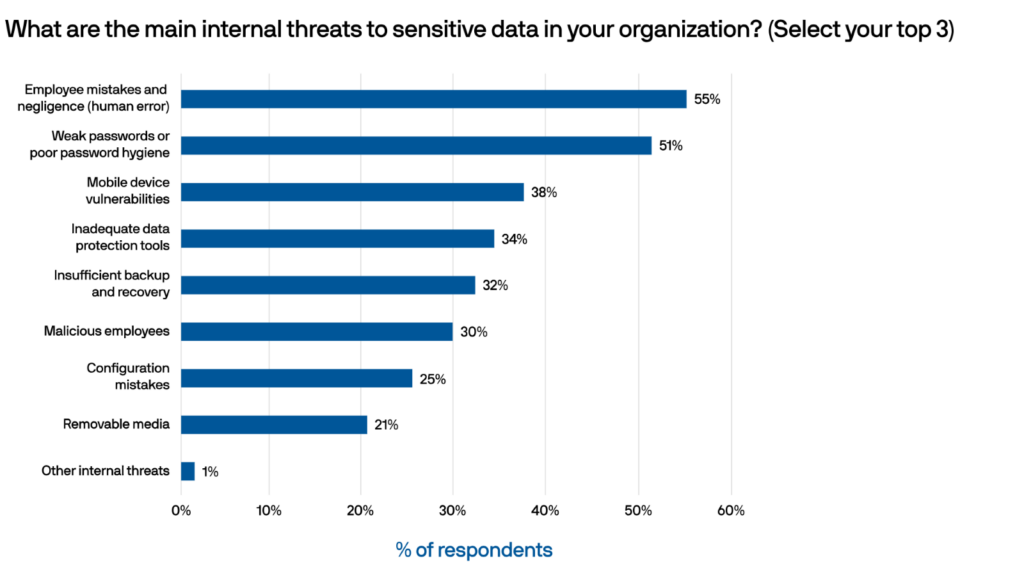
Main concerns with insider threats
While external threats, such as hackers and cybercriminals, are often in the spotlight, it is crucial not to underestimate the dangers posed by insider threats. These internal risks can be just as (if not more) damaging to an organization’s security posture.
Here are some of the main concerns with insider threats:
1. Data breaches and intellectual property theft
One of the most significant concerns with insider threats is the potential for data breaches and intellectual property theft. Insiders with authorized access to sensitive information can easily abuse their privileges, leading to the unauthorized disclosure or theft of critical data.
This can result in substantial financial losses, damage to a company’s reputation, and loss of competitive advantage.
2. Sabotage and disruption
Disgruntled employees or those with malicious intent can intentionally sabotage an organization’s operations, systems, or processes. Whether through the introduction of malware, deliberate deletion of crucial data, or manipulation of critical systems, insider threats can potentially disrupt daily operations and compromise the integrity of an entire business.
3. Insider trading and financial fraud
In industries such as finance, insider threats can manifest as insider trading or financial fraud.
Employees with access to sensitive financial data can exploit this privileged information for personal gain or to manipulate the markets, resulting in significant financial and legal repercussions for the organization.
4. Lack of awareness and detection
Identifying insider threats can be exceedingly challenging, especially when they involve employees who have established a reputation of trust.
The lack of awareness and detection tools can leave organizations vulnerable, as the threats may go unnoticed until considerable damage has already been done.
5. Unintentional insider threats
Not all insider threats are motivated by malice. Some stem from negligence or lack of cybersecurity awareness among employees.
Innocent actions, such as falling for phishing scams or mishandling sensitive data, can inadvertently open the door to potential security breaches.
6. Legal and regulatory consequences
Beyond the immediate operational and financial impacts, insider threats can also lead to severe legal and regulatory consequences. Failure to safeguard sensitive data or comply with industry regulations can result in fines, lawsuits, and damage to an organization’s reputation.
The most vulnerable types of data
Insider threats can pose a severe risk to various types of sensitive information, as malicious insiders with access to such data can cause significant harm to an organization or nation.
Some of the most valuable and threatened types of information include:
1. Defense and military security information
Classified information about national defense, military operations, strategic plans, troop movements, and sensitive intelligence is paramount for national security.
Leaks in this domain can compromise the safety of military personnel, jeopardize ongoing operations, and provide adversaries with a strategic advantage.
2. Intellectual property (IP)
Intellectual property encompasses trade secrets, patents, copyrights, trademarks, and proprietary technologies that give a company a competitive edge.
Insiders leaking valuable IP to competitors or unauthorized parties can severely impact a company’s market position, profitability, and ability to innovate.
3. Trade secrets
Trade secrets are confidential and proprietary business information that provides a competitive advantage and is not publicly known. This includes customer lists, pricing strategies, manufacturing processes, and marketing plans.
Trade secrets being exposed can lead to financial losses, loss of market share, and the erosion of a company’s uniqueness.
4. Financial information
Sensitive financial information, such as earnings reports, merger and acquisition plans, and financial projections, can significantly influence stock prices and investor confidence.
Mishandling of financial information can result in insider trading and market manipulation, leading to legal consequences and reputational damage.
5. Personal identifiable information (PII)
PII includes social security numbers, addresses, financial records, and medical information.
Leaks of PII can lead to identity theft, financial fraud, and privacy violations for individuals, as well as regulatory fines for organizations.
6. Government and diplomatic communications
Diplomatic cables, confidential government communications, and sensitive negotiations are crucial for maintaining diplomatic relations and national interests.
This type of internal data leak can strain international relations, damage trust, and hinder collaborative efforts.
7. Healthcare and medical research data
Medical research data, clinical trial results, and patient records are highly valuable and sensitive.
When healthcare and medical research data is exposed, it can undermine public trust in healthcare institutions, impede medical advancements, and expose individuals to privacy risks.
8. Law enforcement and investigative data
Sensitive information related to ongoing criminal investigations, informants, and undercover operations can be exploited by criminals to evade justice and compromise law enforcement efforts.
Mitigating insider threats: Examples and prevention strategies
Organizations face a significant challenge in mitigating insider threats, as these risks can originate from different sources, including negligence, malicious intent, and compromised insiders.
To safeguard against such threats, organizations must adopt a comprehensive approach involving prevention and defense strategies.
Real-world examples of insider threats are not uncommon. For example, in 2017, the National Security Agency (NSA) suffered a significant data breach when a contractor, Harold Martin III, copied sensitive documents onto his personal devices. Martin’s actions went unnoticed for years, highlighting the importance of proper monitoring and auditing to detect negligent insider activities.
Additionally, in 2019, Capital One experienced a massive data breach resulting in the exposure of over 100 million customer records. The breach occurred due to a former employee’s compromised AWS credentials, highlighting the need for robust access control and authentication mechanisms.
Here are some tips for preventing insider threats before they ever occur:
- Employee screening and training. Implement rigorous background checks during the hiring process to identify potential red flags. Also, provide regular cybersecurity awareness training to educate employees about the risks of insider threats, phishing, and social engineering tactics.
- Access control and least privilege. Limit access privileges to only those employees who genuinely require them for their roles. Employ the principle of least privilege to restrict unnecessary access to sensitive data and systems.
- Monitoring and auditing. Enforce strong monitoring and auditing mechanisms to track user activities and detect unusual patterns or behavior indicative of insider threats.
- Encourage reporting. Create a culture of trust and open communication where employees feel comfortable reporting any suspicious activities or concerns, they may come across.
- Clear policies and procedures. Establish clear and comprehensive policies regarding data handling, use of company resources, and appropriate conduct, and enforce these policies consistently.
- Two-factor authentication (2FA). Require the use of 2FA for accessing sensitive systems or data, adding an extra layer of security to prevent unauthorized access.
While WinZip Enterprise is primarily known as file compression and encryption software, it can also play a role in preventing insider threats through data protection and secure file sharing.
WinZip can assist in mitigating insider threats via encryption and password protection methods, secure file sharing, and data loss prevention (DLP) software.
Try it now and learn how to safeguard your organization’s future from insider threats.
Download our survey today to learn more about threats to your business’ data security.