If you’ve ever encountered a “Data error” message (aka cyclic redundancy check)” when copying data or accessing a drive, you’ve likely wondered what it means. This term is used in data communication to denote an error-detecting code for a cyclic redundancy check, or CRC. This is one of the various techniques used to verify the integrity and accuracy of data transmissions and warn users of potential problems.
A CRC test safeguards against common errors in networks and storage media, such as optical or hard disks. If you see a CRC error, it means that there is something wrong with the drive or the files. Cyclic redundancy check issues often occur when:
- Reading and writing to hard disks.
- Moving or copying files between multiple drives.
- Extracting or downloading compressed files and archives.
Should you encounter a CRC error message, you will be unable to access your data until the problem is resolved. Fortunately, there are several methods you can use to fix cyclic redundancy check data errors.
In this article, we will cover what you can do if a CRC error occurs and how WinZip® Enterprise helps with the troubleshooting process.
How to fix cyclic redundancy check errors
There are several reasons why you might encounter a cyclic redundancy check data error, such as human error or physical damage to the drive itself. This can lead to problems including:
- Drive corruption.
- Registry file corruption.
- File misconfigurations.
- Drive disconnection.
- Program installation failure
No matter the cause, CRC errors need to be taken seriously. If you don’t fix them quickly, you could lose data or experience total system failure.
Before you attempt to troubleshoot CRC errors, be sure to back up any important data to a safe location. Should you be unable to resolve the failed cyclic redundancy check, backing up your data offsets the risk of data loss. Then, you can try the following methods to fix the CRC error.
Run the CHKDSK Utility
Windows comes with a built-in utility tool called CHKDSK. This tool scans for errors in the drive. Once the affected sectors are identified, the CHKDSK scan will try to repair the drive so it will be accessible.
Press the Windows key ⊞ to open your Start menu.
Type cmd in the search bar.
This populates the Command Prompt app in the search results. Select Run as administrator.
Click “Run as administrator” to open the Command Prompt screen.
In the screen that appears, type CHKDSK, add a space, and then the letter of the drive you want to check, followed by a colon (CHKDSK X:). For example, the main hard drive is usually the C drive, so you would type CHKDSK C:.
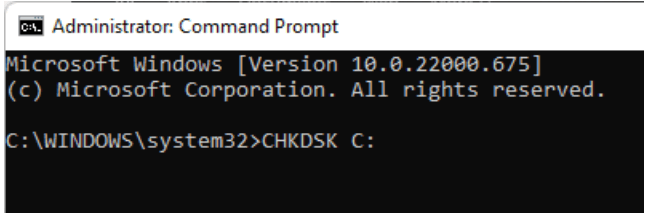
Type in the check disk scan code, followed by the drive you need to check.
Press Enter. The program will run and check the disk for errors, fixing anything that it finds.
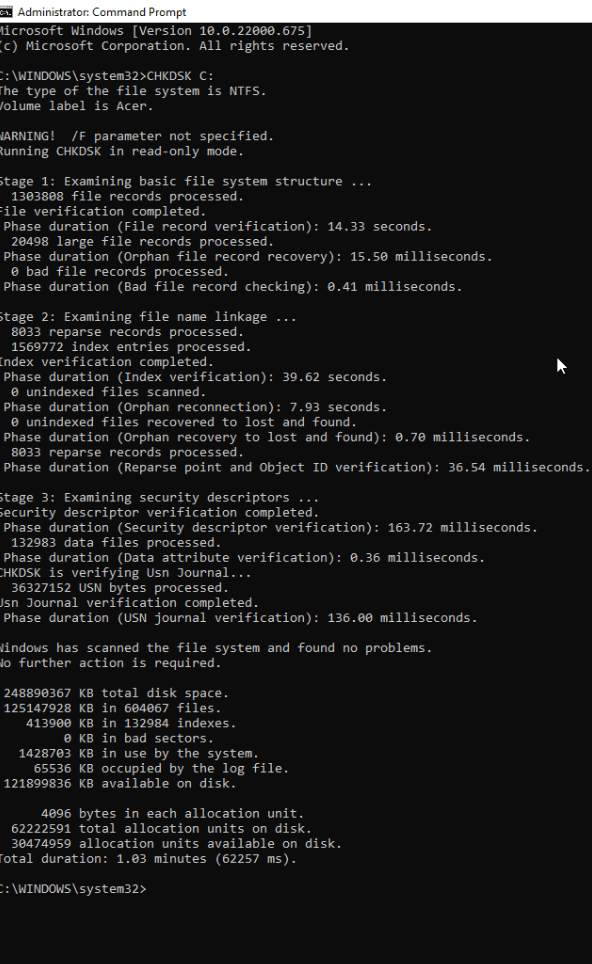
Running CHKDSK is an easy way to correct minor errors.
Note: In addition to the basic CHKDSK X: structure, you can also run the following commands to scan the drive to find and correct errors:
- CHKDSK X: /F – The /F parameter means that the CHKDSK utility will fix any errors it finds.
- CHKDSK X: /X – The /X parameter initiates a drive dismount before the CHKDSK process starts.
- CHKDSK X: /R – The /R parameter tells CHKDSK to find bad sectors on the drive and recover an
If you are still unable to access the files after running the CHKDSK utility to repair errors on the hard disk, there are other ways to complete the repair process.
Use the Disk Check
In addition to CHKDSK scans, you can use the Disk Check utility to find and fix file system errors.
From File Explorer, select This PC and right-click the drive you want to assess. Then, click Properties.
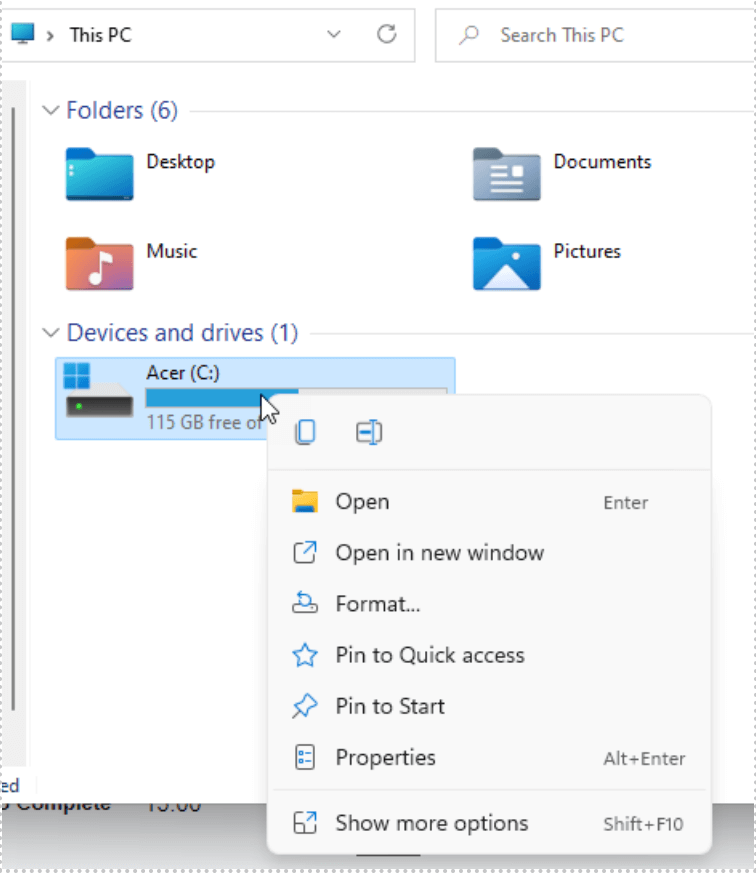
Open the Properties of the affected device or drive.
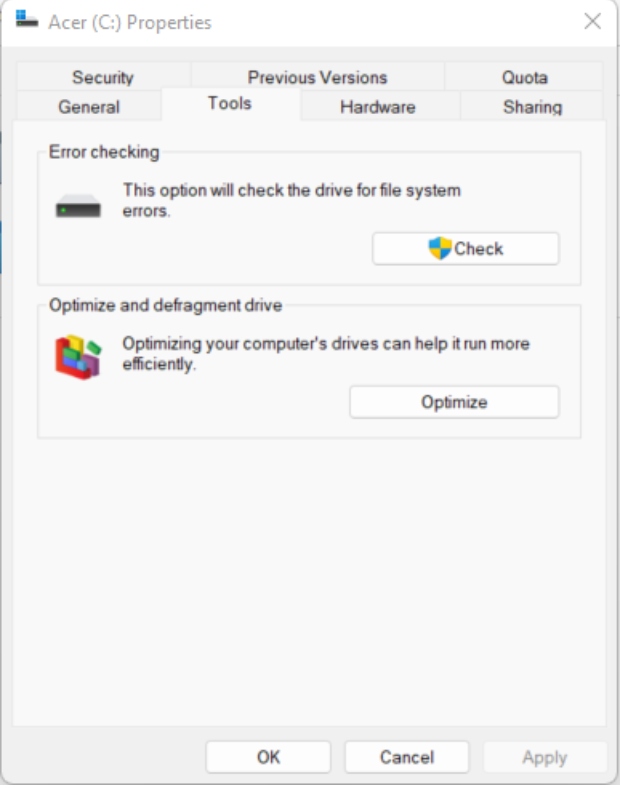
Select “Check” in the Error checking section.
You may see a window pop up that states that you do not need to scan the drive because no errors have been found. You can still run the disk error checking tool by selecting Scan drive.
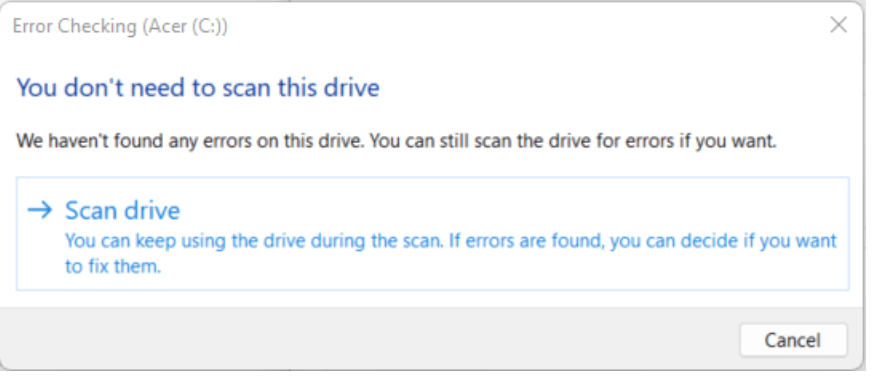
Click Scan drive to run the disk check scan.
The disk check will scan the drive. The amount of time this process takes depends both on the size of the drive and the volume of data it holds.
The scan time is influenced by the size of the drive and the amount of stored data.
If the scan finds errors, the Check Disk tool will attempt to fix them. If no errors are found, you will receive a successful scan message.
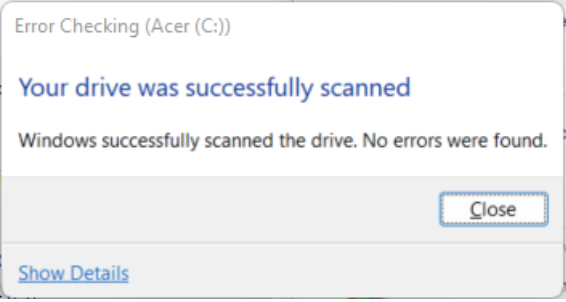
If the drive is free from errors, it is not the source of the CRC error.
Initiate an SFC Scan
The System File Checker (SFC) inspects and repairs system files. An SFC scan is a good idea if the CHKDSK scan did not find anything wrong in the drive itself.
Press the Windows key ⊞ to open your Start menu.
Type cmd in the search bar.
This populates the Command Prompt app in the search results. Select Run as administrator.
Click “Run as administrator” to open the Command Prompt screen.
- In the screen that appears, type sfc/scannow and press Enter.
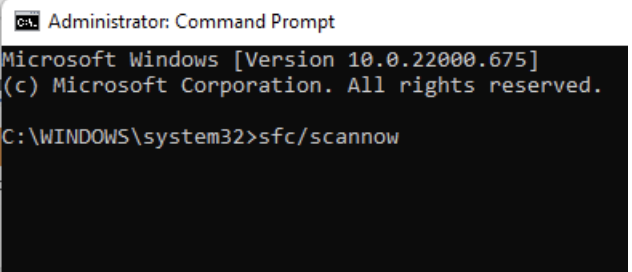
Type sfc/scannow with no spaces to run the System File Checker.
Allow the scan to run. At a minimum, expect a minimum of 15–20 minutes to complete an SFC scan. The exact time depends on the drive’s volume and size.
The SFC utility will repair any corrupted files it finds. Once complete, you can close the Command Prompt window and restart your computer to apply the changes.
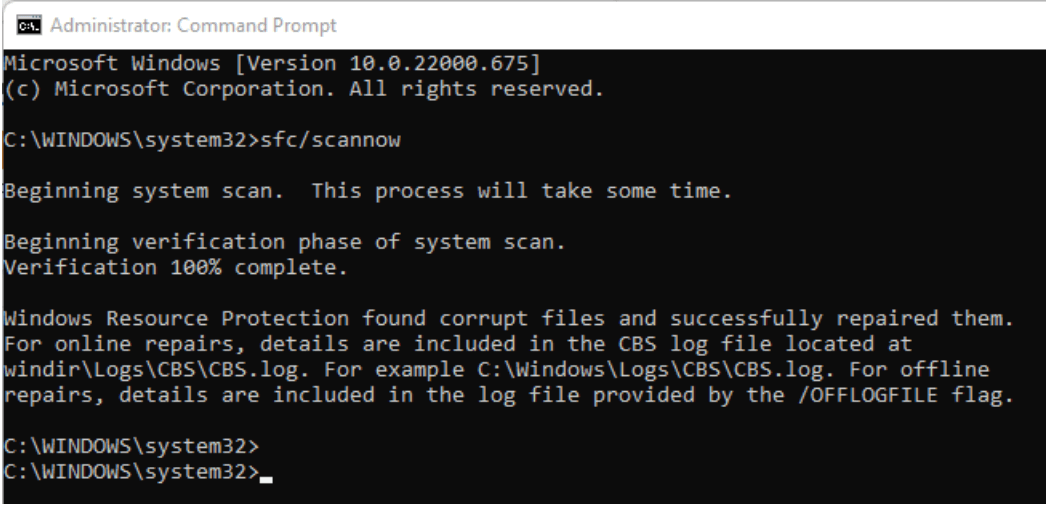
The System File Checker will indicate if it has found and repaired corrupt files.
Format the inaccessible drive
If the above methods have not resolved the CRC error, you may need to format the drive itself. Formatting will erase data stored on the drive, so be sure to create a backup before reformatting.
From File Explorer, select This PC and right-click the drive you want to reformat. Then, click Format.
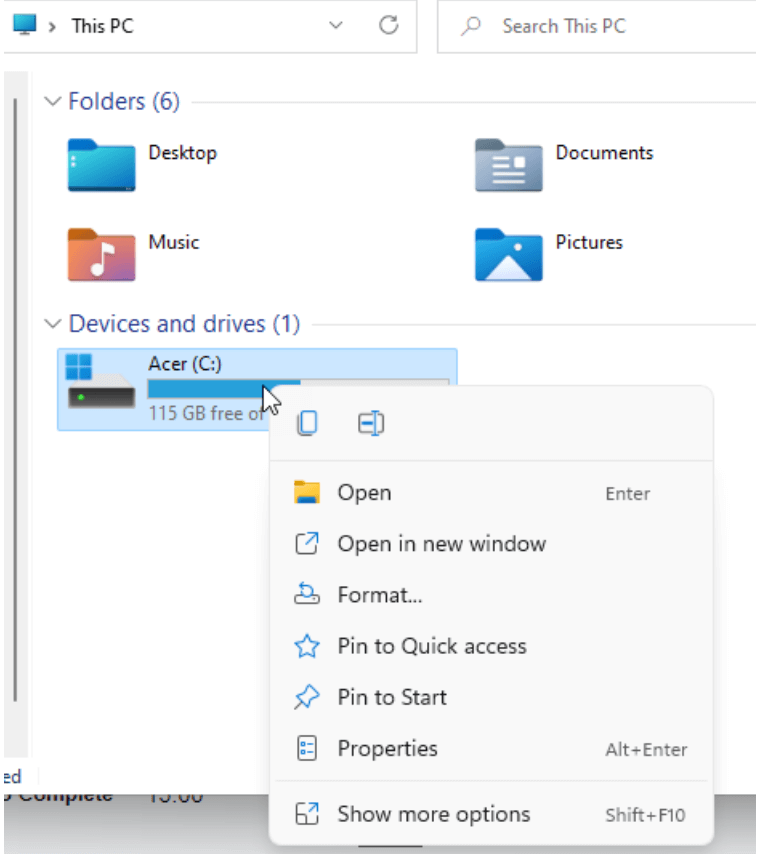
Select Format after right clicking on the affected drive.
-
Note that you cannot reformat the drive that Windows is installed on (it is typically located on your C drive). If you attempt to format that drive, you’ll receive the following error message:
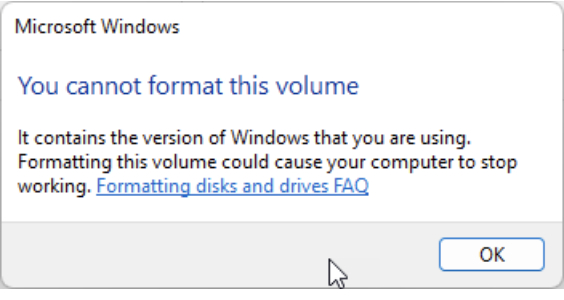
You cannot format a drive that has Windows installed on it.
-
Enter the drive name in the Volume label textbox.
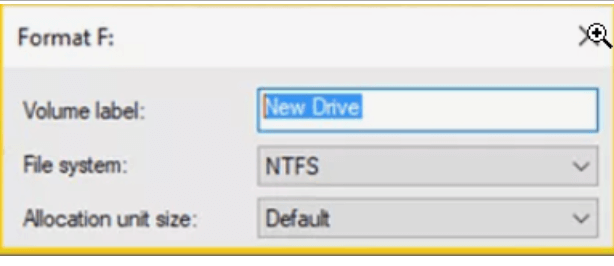
The Volume label represents the name given to the drive.
-
Select the appropriate file system, which is almost always NTFS. FAT32 is rarely used.
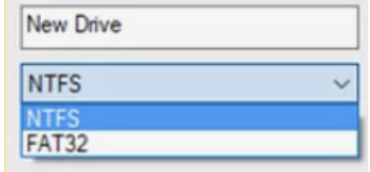
Select NTFS in the File System drop-down.
Decide if you want to run a quick or standard format. When it comes to failed cyclic redundancy checks, the standard format will ensure that every sector of the drive is scanned for errors.
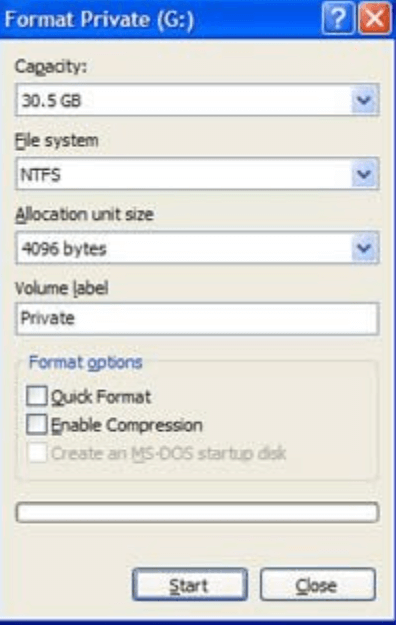
Leave the Quick Format box unchecked if you want to scan the drive for sector errors.
When you’re ready to reformat the drive, click OK. A warning message will appear to remind you that reformatting erases all data on the drive.
Review the warning message and click OK to proceed with formatting.
Quick formats typically only take seconds to run. However, the time required to run a standard format depends on the drive’s size.
How to fix CRC errors when extracting files using WinZip Enterprise
While the previous methods focused primarily on corrupted drives and devices, you may also receive a CRC error message when extracting or downloading a Zip file. This is because WinZip compares the CRC value of the extracted file to the value of the zipped file. If there are differences in the two CRC values, WinZip generates a CRC error message because the extracted file does not match the original file.
Should you encounter a CRC error message, you should first try to obtain another functional copy of the file. You can do this by pulling from your backup copy or the original source. If you cannot download a new copy of the file, you can use the WinZip Repair Tool to repair the corrupted file.
Also, you might try redownloading the file in case the CRC error stems from corruption during the download process. This would suggest that the issue was an internet connection or server problem. If this is the case, redownloading the affected Zip file will usually resolve the CRC data error.
Files and drives can be damaged at any time, making it impossible to avoid the possibility of CRC errors. However, you can minimize the risk by leveraging WinZip Enterprise to secure and manage your files.
In addition to best-in-class file compression and encryption capabilities, WinZip Enterprise offers a host of features to simplify file sharing and protect important data. For example, thanks to WinZip Secure Backup, you can always retrieve an uncorrupted copy of your data should you experience a CRC error.
Discover how WinZip Enterprise can help solve cyclic redundancy check errors and other data issues.





